Immutable Storage Solutions for Ransomware Protection
Posted December 16, 2021 by Sayers

Worried about ransomware? You have good reason to be.
Worried about ransomware? You have good reason to be. According to the FBI’s annual Internet Crime Report, the bureau received nearly 2,500 ransomware complaints in 2020, with a reported collective cost of the attacks at more than $29.1 million.
Lost data means lost revenue. Organizations that had backups but couldn’t quickly complete their disaster recovery resorted to paying the ransom, rather than keep losing money while trying to get their environment operational again.
For strong data protection, think of immutable storage. A variety of immutable storage solutions offer the ability to use policies to prevent any deletion or alteration of your data, so you can get up and running after a disastrous business disruption.
Immutable Storage Isn’t New, But the Threats Have Changed
Immutable storage has been around for a while. You were using one form of it if you’ve used a write-once-read-many (WORM) technology with your tape system. Each of the big three public cloud providers – AWS, Microsoft Azure, and Google – offer some form of immutable storage.
Many industries, particularly healthcare and government, have used it to meet various regulations and compliance requirements. Now the stakes are higher and affect a broader range of industries that rely on data as the new resource of our information age.
Criminals go for the money, so they’re going for your data. Organizations need immutable storage as a line of defense to ensure their backups are safe and preserved against malicious ransomware attacks.
Three Basic Components of Immutable Storage
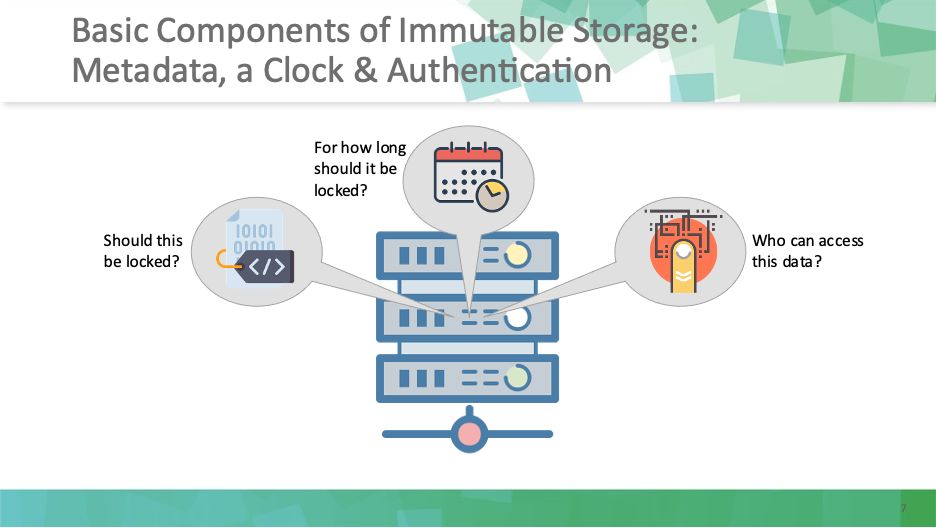
What makes storage immutable comes down to three key features: • Metadata. Should this item be locked? Should this data be immutable, to begin with? The answers can depend on the type of data it is, and what folder or container it resides in. • A clock. How long should the data be locked? Immutable doesn’t have to mean forever. Your organization determines if the immutable storage solution has a policy that makes the data immutable for a specific number of days or years. Avoid this painful mistake: If you have a policy to retain the data for seven years, don’t set your immutable storage to be forever, or you won’t be able to reclaim that storage after the seven-year period expires. • Authentication. This refers not only to who can access this data but also to who can alter it. Who even needs to be able to see it? Weak authentication such as simple passwords or poor role management can compromise otherwise immutable storage, as bad actors will look for a way to exploit this.
Immutable Storage Or Air-Gapped Data? Use Both.
There’s an ongoing debate about immutable storage vs. air-gapped backups. Think of it as a security debate between the pyramids of Egypt vs. a remote island. Immutable is unalterable, like the pyramids that have remained essentially unchanged for thousands of years. Immutable storage prevents anyone from editing or deleting your files after you’ve uploaded them.
Air-gapped backups are remote isles. They make it difficult if not impossible for malicious hackers to access the data on your server remotely.
Which is better to have? You need both. Together, immutable storage and air-gapped data provide the best of both worlds. Build that pyramid on a remote island. No one can get to it, and even if they somehow do, it can’t be altered.
Factors in Choosing Your Immutable Storage Solution
Current options for immutable data protection fall into three main categories: • Immutable backups on your primary storage: These preserve a portion of usable disk space for volume snapshots on your primary storage. They offer the fastest recovery, but they’re the most expensive option. • Backup software solutions: These use APIs to interact with the storage platform and activate the immutable features on the hardware. Highly flexible, but performance depends on the underlying components. • Data protection appliances: Based on hyper-scale architectures, these essentially are software solutions with specific hardware builds and are designed to own the file system. Not as flexible as traditional software, and not as expensive as primary storage. Which solution you choose depends on your needs for rapid recovery vs. long-term archiving. Two key metrics to consider are your recovery time objective (RTO – how fast you need to recover your data after a business disruption such as a ransomware attack) and the recovery point objective (RPO – how recent the backup snapshot of your data needs to be). Other considerations include regulations and compliance concerns for your data. You’ll also want to determine if you need multiple solutions for different parts of your organization or one solution with single-pane-of-glass visibility and management. Some solutions are easier to learn and implement than others, so make a point to evaluate your staff’s skillsets. Does your team have the time to learn, implement, and operate a new solution while maintaining existing infrastructure?
Reality Check: Immutable Storage Isn’t Enough
Immutable storage provides the foundation for your data protection. But you also need complementary technologies and methodologies to protect your data against ransomware and other outage causes.
Prioritize with a focus on policy, which includes pre-defining your RPO and RTO before the disruption occurs. RPO and RTO provide the measurable outcomes you can design your solution to deliver.
As mentioned earlier, bad actors can undermine the immutable storage for your backups by exploiting weak authentication or poor role management.
If ransomware attackers can access the storage solution, they potentially can alter the data retention policy or solution configuration to render it ineffective. Or they might try to compromise the switches that provide network access for your rapid recovery.
For those reasons, you need monitoring and analytics to know whether your environment has been compromised. Identify who’s monitoring your data change rate and how they’re doing it. Establish the baselines for your system’s normal behavior, what triggers an alert, and who acts on it. With this structure of monitoring and response in place, you can get in front of bad things if they happen.

Bottom line: The sooner you’re aware of a problem, the more likely you can prevent it from becoming a drawn-out disruption that makes paying the ransom seem like a better option.
For more on this topic, watch the 19-minute “Immutable Storage and Ransomware” presentation from the Sayers #CURIO Virtual Tech Summit, now available free on-demand.
Questions? Contact us at Sayers today. We can answer your business continuity questions and help you with your data protection decisions.


